The need to assign access to content and data is fundamental in enterprise analytics. Pyramid drives access to functionality, content and data through a user-role based model (even if the source of users and role assignments are driven by external security infrastructure like SAML and Active Directory). The unified approach to security makes it very effective and simple to construct sophisticated access scenarios for the entire "data to analytics" pipeline in a single application.
Enterprise Integration
Many enterprises already have security apparatus and frameworks for authenticating users. Pyramid integrates with many such solutions out of the box (SAML, AD, LDAP etc), while its security APIs can also be used to build custom authentication and access solutions (see below). This integration is very much part of the unified approach to security.
Unified Security Model
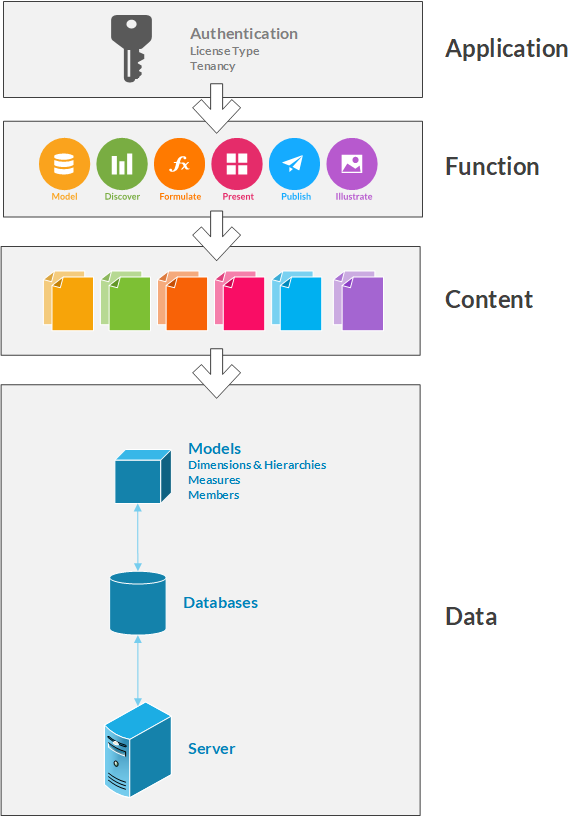
Pyramid's unified security model brings together 4 tiers of settings that control the way users can access analytic content. While the same role model is used in a common way throughout the application, the role settings can be applied independently for each of the main tiers of security in the application.
For example, a user may have functional access to the Discover tools, they may not necessarily have access to all Discover content. And while they may have access to a specific Discover report, its possible they cannot see all the data in the report's data source since it is limited by security. Indeed, access to the content WITHOUT access to the data, renders the report useless.
- Application Security: governs access to the application itself; sets the type of user license type (pro vs viewer); and tenancy.
- Functional Security: governs what apps a pro user can access and specific functions within each of those apps
- Content Security: governs which content files (and folders) users (both pro and viewer) can access in both the workgroup and public content domains.
- Data Security: governs which data servers, then databases and then data models users (both pro and viewer) can access. Within data models, the governance extends to which dimensions (tables), hierarchies (columns), measures (values) and even members (row items) users can see.
Configuring Security Rights
Application Access
The authorization to access the application itself is set through the user and roles manager in the admin console. It is set by admins only. To gain authorized access, users need a Pyramid pro or viewer license (which itself determines high-level functional capabilities). The authorization process also includes tenant settings (which can be different between tenants in a multitenant deployment).
Authentication of users is highly related to authorization, but is a different set of concepts, functions and settings.
Functional Access
The functional rights of pro users is set via the user profiles of pro users in the admin console. It is set by admins only. Here, admins can delineate which apps, and which key functions of each app are accessible by user (or by role).
Content Access
The read, write and management access rights of all users to content is set via the roles panel in the content manager.While access to the workgroup content domain is purely driven by inclusion within a role, access to the public content domain is driven by verbosely giving different roles access to different folders and content items within those folders via the content roles panel. Root access in public folders is initially determined by admins, other non-admin users can be delegated management rights to folders and items to manage other roles on the system.
Viewers on the system, are only given READ access to content, Pro users can independently retain WRITE access to content as well, even if they are not entitled to change any other role's rights to specific public content.
Data Access
In principle, all data access settings for roles are driven by admins through the data source tools and Data Source Manager in the admin console. However, if pro users are given the rights to create their own data sources (a profile setting in its own right), non-admin users can manage their "personal" data sources or any data sources they have created through the "Materialized Content Manager" - which is a slim down version of the Data Source Manager.
Unlike normal users, much of the security apparatus does not apply to admins - who have open access to all functions, content and data. The only limitation is that "domain" admins, in a multitenant deployment, have full access to things within their tenancy only.
Security Automation
Security APIs allow all of the above settings to be created and edited programmatically to configure each layer of security in the application:
- Authentication APIs - are used to manage how a user logs into the system and gets their authorizations.
- Access APIs - are used to create and manage users, roles and profiles (for general and functional access)
- Content APIs - are used to manage access to content items and folders
- Data Source APIs - are used to manage access to data sources